Don’t feed the Phish
Digital Literacy and Online Safety (Y7) - Lesson 2
A note about this lesson

This lesson is taken from Common Sense Education’s excellent Digital Citizenship curriculum. Their resources are shared for free under A Creative Commons Attribution- NonCommercial- NoDerivatives 4.0 International License.
You can find the original resources HERE.
Objectives
- Compare and contrast identity theft with other kinds of theft.
- Describe different ways that identity theft can occur online.
- Use message clues to identify examples of phishing.
Lesson 1 - Finding Balance in a Digital World
Lesson 2 - Don’t feed the Phish
Lesson 3 - Who are you online?
Lesson 4 - Chatting Safely Online
Lesson 5 - Digital Drama Unplugged
Lesson 6 - Finding Credible News
Links to Education for a Connected World.
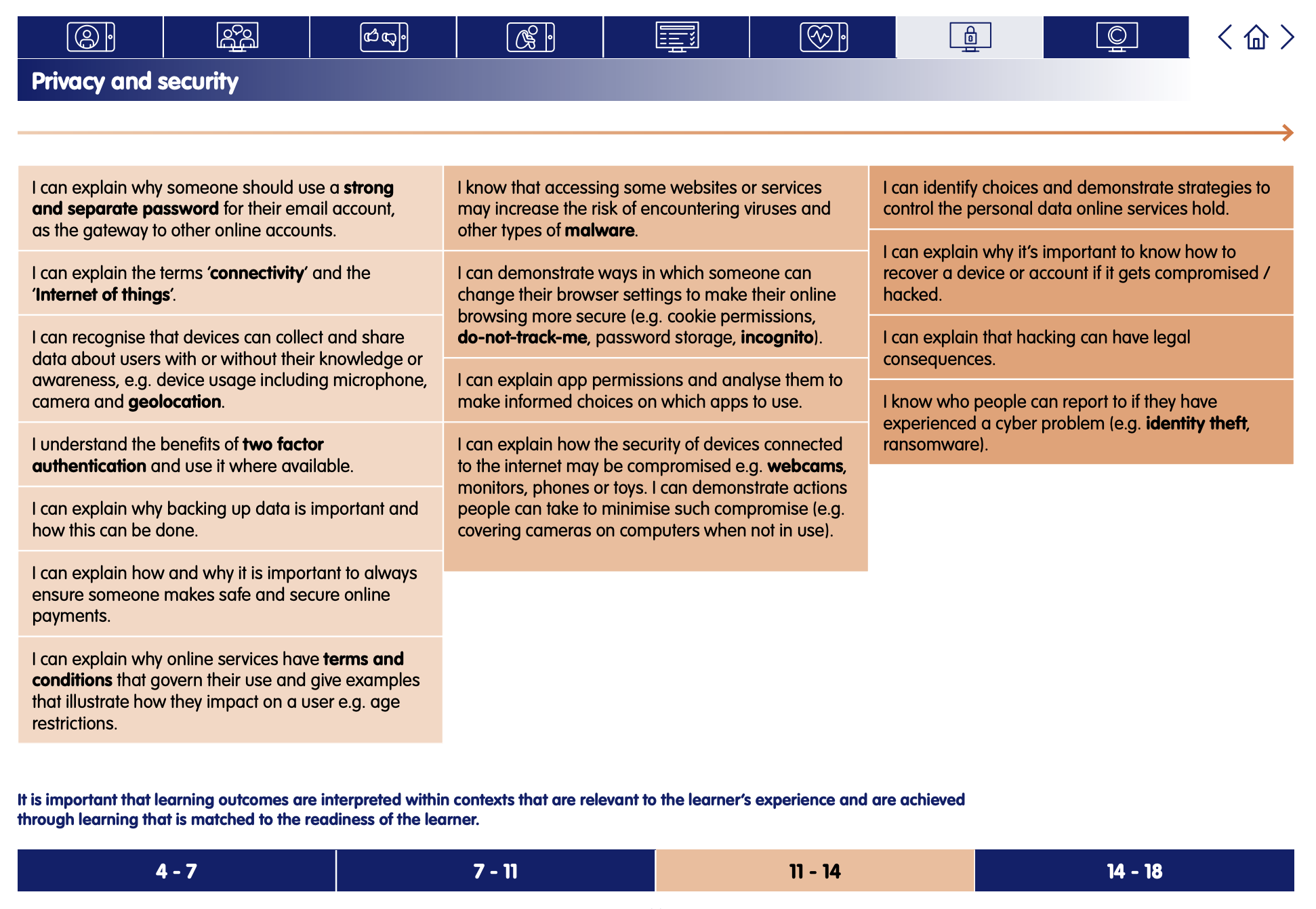
This lesson from Common Sense Media's Digital Citizenship curriculum links to the following strands from the Privacy and Security section of the Education for a Connected World framework.
Introduction - Safe or Unsafe?
Project Slide 4 and read it aloud: What's something you own that someone else might want to steal? Why? What would they do with it? Take turns sharing your idea with your partner.
After students pair-share, call on a few of them to share out with the class. Students may respond by naming things of value that they own (clothing items, electronics, etc.) and how they might be used.
Say: In reality, the thing you own that might be most valuable -- and most likely to get stolen -- is not a thing at all: It is your identity. What do you think that means? How could someone steal your identity?
Call on students to respond. Students may say: It means that someone can pretend to be you or Someone can get your information.
Follow up by asking students to explain more and clarify any misconceptions. For example, identity theft might mean that one or more pieces of information about you has been stolen, not that everything about you has been. It also doesn't mean you no longer have what's been stolen (as in the case of a stolen object); you are still you and your identity hasn't changed.
Project Slide 5 and define identity theft as a type of crime in which your private information is stolen and used for criminal activity.
Ask: What do you think is meant by "private information"? What would an example of that be?
Call on students to respond and provide examples. Define private information as information about you that can be used to identify you because it is unique to you (e.g., your full name, phone number, or address). (Slide 6)
Say: Identity theft is important to know about, because if your identity is stolen, it can lead to some pretty bad consequences. And you may not even know about those consequences until far into the future. If your identity is stolen, it could potentially enable someone to: (Slide 7)
- steal money from you.
- apply for credit cards in your name and buy things.
- cyberbully someone while pretending to be you.
- create false identification documents.
- apply for loans (to buy a car or house).
- get a driver's license or a job under your name.
Say: Now that we know what identity theft is, let's talk about how it happens and what you can do.
Main Task - How Identity Theft Happens
Say: One way that someone can try to steal your identity on the internet is by getting you to click a link or enter information about yourself. This is called an internet scam (Slide 8), which is an attempt to trick someone, usually with the intention of stealing money or private information. Let's see how this can happen.
Have small groups collaborate on the Trick Questions! Practice Quiz Student Handout. Allow students two minutes to complete the activity. Most students will quickly recognise that "DON'T!" is the right answer each time.
Challenge them to figure out reasons each character in each scenario might have gotten fooled by the scams. Students may indicate the following reasons:
- the wish to win money, a prize, discount, or other benefit.
- the fear of losing one's photos, videos, games, or access to their account.
- feeling pressure to act quickly "before it's too late."
- curiosity to know more.
Identify the last point as the curiosity gap, which is the desire every person has to figure out missing information. Explain that online messages are often designed to trigger your curiosity gap so you will click a link to find out more. Give examples:
- a tweet that asks an interesting question.
- a photo with the caption "Funniest thing ever!"
- a video pop-up that says "To continue watching, click here."
Tell students that the link may lead to a site with false or misleading information, or to a site that is malicious or harmful. These sites let identity thieves steal your personal information and, sometimes, your money.
Explain that one of the most common ways identity thieves get your private information is through something called phishing (when someone poses as an institution, such as a bank or school, and sends you a personalised message asking you to provide private information).
Students might think of phishing as similar to fishing -- someone trying to "catch" people's private information like trying to catch a fish. (Slide 9)
Project the samples messages on Slide 10. Have students work in small groups to decide whether to click on or skip the various links shown and why. Encourage them to pinpoint which details helped them decide.
They should identify only the Mari Tellez example as one that is likely OK to click.
Explain that some links, or URLs, are not what they seem. Ask: Why do you think the links might trick someone? Define shortened URL (Slide 11) as a web address that has been condensed and which could potentially mislead a user into going into a risky website.
Explain that such a website may:
- install malware on your device.
- steal your information.
- charge you money.
Say: In the next activity, you'll learn strategies for protecting yourself against phishing and identity theft.
How to Catch a Phish
Distribute the How to Catch a Phish Student Handout and focus students' attention on the list of clues. Allow one minute for students to read the list of clues and answer any questions they have.
Tell students that they will work in pairs to analyse examples of messages that use tricks to phish for your information. (Slide 12) Model how to highlight a clue in the message, and list the type of clue in the empty box. You may wish to have students colour-code the clues.
Allow pairs time to complete the activity on the handout.
Call on students to share their answers. Use the Teacher Version to support students in using specific details from each example.
Summarise how checking for clues that indicate phishing can help protect you from identity theft.
Extension Activity:
Have students apply what they have learned by completing the “Scams and Phishing” Activity on TestDrive, a social media simulator. Students go through a self-guided activity to reinforce key concepts and practice protecting their private information. For more information, download the Social Media TestDrive Educator Guide.
Plenary- Stay Safe from Scams
Say: You have learned about the importance of protecting your information from identity theft. You also have learned strategies for guarding against phishing scams. Now use what you have learned to show how others can protect themselves against identity theft.
Project Slide 13 and read aloud the questions. Allow students a few minutes to answer and then collect to assess student understanding.
Assign the Google Classroom Quiz (and view student results via the quiz link). Or, adapt the Teacher Version for your own quiz tool.
Send home the Family Activity and Family Tips.